Evaluating the ASA Botnet filter Cisco ASA Botnet filter test and evaluation When the ASA Botnet filter feature was announced I thought that it's an interesting concept and is definitely worth trying.
- 'White' IP addresses are let through and 'gray' are dropped or permitted based on the configuration. By default graylisted traffic will be permitted. The syslogs related to Botnet filter are%ASA-4-338001 up to%ASA-4-338008 and ASA-4-338201 up to ASA-4-338204. No syslogs or statistics will be generated for 'unknown' traffic.
- The Cisco ASA appliance with the Botnet Traffic Filter should be deployed at the edge of the enterprise, as the botnet database contains information only about external botnets. It is also best to address the external threat as close to the source as possible.
This looks VERY cool. The ASA has a built-in Botnet filter.
2 Steps total
Step 1: Get the license.
With the latest image, asa821-k8.bin, the ASA now has something called a 'Botnet filter'. You need to purchase a license for it but retail from Cisco it is only $130.00.
Step 2: Configure the ASA
There is a nice doc on this at Cisco's site (attached).
http://www.cisco.com/en/US/docs/security/asa/asa82/configuration/guide/conns_botnet.html
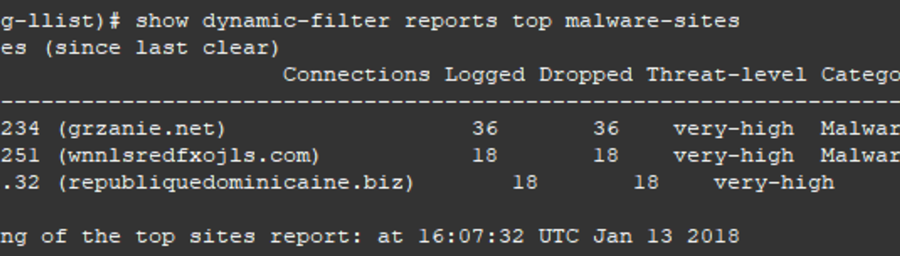
Once this feature is configured it will poll a Cisco dynamic database of known bad sites and block and log accordingly. There is also a static list you can maintain yourself. These can be used at the same time.


Another tool to fight with the bad guys! If you do this or have it working post your results!
Botnet Server
8 Comments
Sonicwall Botnet Filter
- CayenneKevinRitchey Jan 7, 2010 at 02:53pm
Looks good. I'll be trying it out next month.
- Jalapenotyniem Jan 29, 2010 at 07:22pm
I'm in the same boat - looking to try it in the next month or so. Obviously it's not the be all end all of protection, but with a layered approach, it should help.
- Sonorarite99 Feb 21, 2010 at 01:46am
I have Trend Micro installed in my ASA5510, does this botnet is a hardware module as well? and which is better the trendmicro or botnet?
- TabascoPCMonk Feb 22, 2010 at 08:34am
It looks like the Trend product is built and used in the IPS module installed in the ASA. I know nothing about it. What the bot net filter does is pull a list of known bot net domains from Cisco and then block access to those domains. I think the ASA module would already have this capability build in.
- Jalapenotyniem Apr 1, 2010 at 01:01pm
Took me longer than expected to install. Long story short - I'm hooked on the Botnet Filter. Wemigrated from Smartfilter to OpenDNS. The Botnet filter helps fill in the cracks. Do yourself a favor and upgrade to 8.2.2 - reporting is much better than 8.2.1 and you can automatically shun malicious traffic. 8.3 is available - but requires a memory upgrade. Good luck.
- PimientoTim7091 Apr 10, 2010 at 09:45am
Botnet filter is service that runs in software on the base ASA; that is, is does not make use of the hardware slot nor does it conflict with either the Trend or IPS blade which can be installed.
This functionality differs from anything else found on the Trend or IPS blade; though the IPS blade does contain SensorBase information for further layered security.
- MaceBryan Doe Oct 20, 2010 at 09:09am
Pretty slick stuff - I'd never heard of the filter until I saw this. Definitely one of the lesser-known licenses. Still, for under $100, I think it's worth it. With any luck it won't be blocking much, but what it does will be extra piece of mind.
Setup is easy - the Cisco document in the how-to isn't hard to follow.
- Jalapenoace-brown Oct 29, 2012 at 01:21pm
I've been considering this. Thank you all for posting on it. I'm going to be doing some hunting on a few of our servers because I'm seeing some suspicious activity on a server that normally gets little or no use at this time. This server however faces the web so it may have gotten infiltrated... I'll be trying a TrendMicro botnet scanner if there is a free tool out there. I will also check with Vipre. Does anyone have suggestions about botnet detection and removal? I've just started doing my research and any tips/experience would be helpful!
Botnet Server List
Botnet Filtering on ASA: Reputation based filtering
Cisco has Security Intelligence Operations known as SIO
Inform, protect and respond
Early-warning intelligence, threat, and vulnerability analysis, and proven Cisco mitigation solutions to help protect networks.
They collect information about malicious traffic patterns all over the world and try to identify the people who are responsible for it.
We need to train ASA to identify malicious ip address and stop any traffic going from pc to that device.
To implement this on ASA, we need to have SIO based infrastructure and need to buy time-based license.
Basic requirements:
ASA should have reachability to cisco server to download dynamic database.
How it works?
DNS on the ASA: to resolve the name of cisco server
Turn on “DNS Snooping” : ASA will look out for each DNS request that customers are making out to the internet
Enable Client and use dynamic database
Optionally create static lists
Specify action in regard to interface
ASDM :
1. Config -> Device Management -> DNS -> DNS Client -> Add info
Primary DNS server : 8.8.8.8
Enable on outside interface
2. Config -> Firewall -> Botnet Traffic Filter -> DNS Snooping : for botnet option we need license
3. Config -> Firewall -> Botnet Traffic filter -> Botnet Database
4. Config -> Firewall -> Botnet Traffic filter -> Black and White Lists
5. Config -> Firewall -> Botnet Traffic filter -> Traffic Settings: to specify interface on which traffic to be blocked
